1. Prerequisites
2. Start PuTTYgen
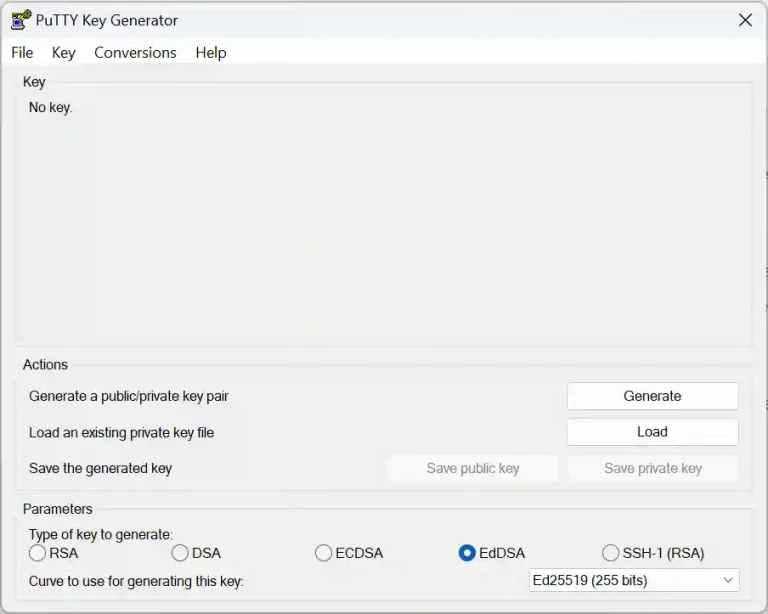
3. Choose the type of key to generate
4. Generate the key
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIC7OlzesPfehPyD87m0uGElWk13BPpiTAg0ydLHchkNO eddsa-key-20240401
Note there are no carriage returns in the text, only spaces.
5. Save the Keys
It seems intuitive to click <Save public key> to save a text file containing the public key but note this will not save the key in a format that can be imported to Authorized_keys. Copy the text from the Key box and save and use this.
If you have access to the console of the device you wish to enable eccess with keys the easiest method is to execute the following comands:
mkdir -p ~/.sshecho ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIC7OlzesPfehPyD87m0uGElWk13BPpiTAg0ydLHchkNO eddsa-key-20240401 >> ~/.ssh/authorized_keysNow lets secure the directory and file so that only the used has access to the files. First remove group and other rights to .ssh recursivley.
chmod -R go= ~/.sshThe owner of the directory and files withingn it should already be set but just to be sure replace owner in the following with the user you are logged in as:
chown -R owner:owner ~/.ssh